Optimisation and Personalisation Tech Lead
Blatantly asking the same question again and again, is a sub-standard experience. I’m looking at you ‘cookie banners.’ So where does identity fall into all of this? Let’s take a look at some broad identity lifecycle stages
When you walk into a retail store for the first time, you’re a fresh new face to the business and the staff on deck that day. Ideally, they greet you, welcome you to their store and politely offer their assistance, should you want it.
If you go to the same store often enough, the staff may recognise you and even get to know you a bit. They may ask questions or comment about some personal subjects based on your previous shared conversations or the products you’ve purchased or just looked at before.
How do you do that on a website or app?
How do you do it without being annoying?
How do you do it without being creepy?
I once worked with a company that had grand visions of using store security cameras to run facial recognition on all incoming people. The aim was to arm staff with tablets running a custom app that would automatically bring up customer profiles including cross-channel, past purchase and even medical data, “to better serve (or was it sever?) the customer”.
I don’t know about you, but that crosses the ‘creepy’ line for me.
Especially if I’m not asked for my permission or don’t feel I can trust the company to honour my choice. Equally, if I’ve been asked before and declined my consent for this type of identification, tracking or data sharing, I’d be super annoyed if I was asked every single time I walked into the store. Wouldn’t you?
The same is true for web & app. By all means, you should test different approaches to the way you ask for permission and you should drop little hints along future encounters to spruik the benefits of consenting to some sort of permission. But blatantly asking the same question again and again, is a sub-standard experience. I’m looking at you ‘cookie banners.’
So where does identity fall into all of this? Let’s take a look at some broad identity lifecycle stages:
- Unknown Unknown
- Known Unknown
- Identified
- Authenticated
- Authorised
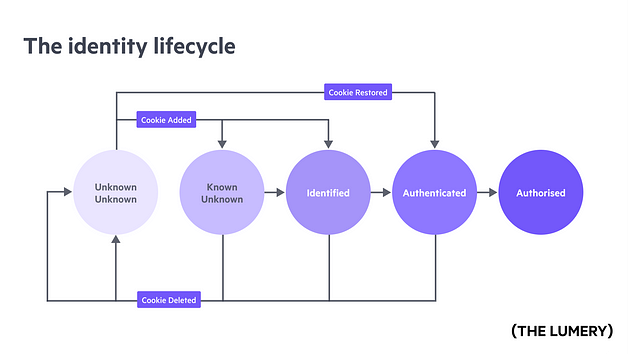
Unknown Unknown
When visitors first arrive at your store, they’re ‘unknown-unknowns’ — meaning you know nothing about them. On that first visit, you may ask for their consent to personalise their experience based on their behaviour or other similar consent related questions. For example, you may ask them for:
- Digital Tracking Consent
- Personalised Marketing Consent
- Channel Consent (email/sms/push)
- Third-Party Data Sharing Consent
If they don’t answer, you may choose not to collect any information about them or you may choose to collect anonymous data about them — this choice depends on your company’s ethics, privacy, terms of use and regulatory policies.
If they do answer, you need to remember and honour that choice as much as possible. In the online space this is done partly with cookies. This means, if they return to your site/app on the same device/browser, you’d ideally not ask the same question again and just enforce their preference. If they arrive via a different browser/device you will need to ask them again, as the cookie won’t exist. But this should be a reducing exception rather than the norm.
As a digital marketer, at this point you may think, “well great, we can’t do anything with these unknown people, so what’s the point in honouring their consent choice unless I’m required to do so by law?” To this, I say customers are becoming savvy to the value of their data to businesses and they want to know: “What do I get in return?”
As an expert in this field, I regularly ask marketers, product owners and ELT, what are you offering in return? Are you going to ignore this question until the threat of regulatory compliance is forced upon you? Or will you opt for the “soft-sell approach and treat this identity lifecycle as a preliminary purchase funnel. One where the conversion metric is measured by obtaining digital identification and marketing consent.
In some cases, this soft-sell approach may come in the form of premium content, special offers, discounts, loyalty points, etc. Whatever it is, there needs to be one or more reasons to elicit that informed connection by your customers.
Known Unknown
So, what comes next? If your organisation is comfortable with collecting anonymous data about a visitor and your governing legislation allows, there’s another stage in the identity lifecycle. This is where visitors have visited before, and you’ve started to know them based on the products, pages they’ve browsed or questions they’ve asked. Now they are “known-unknowns”. This means, even though you still don’t know who they are, you can tailor their experience based on their previous interactions. With the right tools, you can even tailor their ‘entry page’ based on the content they’re interested in, even if they opened it ‘organically’ and not through a click on a call-to-action.
Enter, ‘Lookalike Modelling.’
You can compare anonymous data about their visit with other visitors who came from the same location, device, time of day, etc or took the same path through your store. This is still highly valuable information.
Unlike the physical world, you can reorganise your digital store, differently, for various groups of anonymous users while honouring their preference not to be tracked personally.
This is huge.
It’s far more than many companies are doing online today. It has been proven, many times over, to increase engagement & drive revenue uplift in every company I have seen implement it.
And, depending on your interpretation of the GDPR, it’s compliant as long as you remove any identifying information when storing the data for mining.
Of course, better still, it encourages visitors to identify themselves by signing up to your newsletter, website or app.
Identified
What is the digital definition of “identified?” At its simplest form, a customer ‘identifies’ when they provide a ‘unique’ piece of information about themselves. This is most often an email address or phone number in a ‘contact us’ or ‘subscribe to newsletter’ type form. Of course, ‘householding’ is an issue that needs addressing as some people share emails and phones with their partners. As a business, you need to understand whether you need to identify such people individually or can address them as one ‘household’.
Regardless, just because you collect these identifiers doesn’t mean you can use them for marketing. You need explicit consent for this, so all such forms should present the relevant ‘marketing consent’ checkbox de-selected and allow the visitor to explicitly consent if they choose to.
Once identified and consent obtained, you can begin tailoring the content of your store individually, for every, single, customer.
While this is an even bigger improvement, it still has the downside of failing to identify the same visitor across new devices, apps or sites. It also has the potential to ‘forget’ the visitor if they clean their cookies or site data.
Authenticated
For the most consistent experience across channels & devices, you want your customers to create an account with your brand or service. Not just to get some gated content or begrudging access to your services. But because they trust you, they value your content and the benefits that authentication provides. With the rise of ‘disposable email address’ services, now it’s more important than ever to review your value proposition.
By logging into an account, you can restore all of their preferences, from their profile, across all of their devices — even if that preference is to opt-out of everything.
Once you can consistently recognise who they are, you can continue to test new strategies to convince them that granting their consent is the right choice for them.
Authorised
This term refers to getting access to an area of the site or app based on who the person is. Most of you are familiar with the ‘teaser article’ approach, where anonymous visitors get to see a portion of the article unless they login or pay. Other companies, show a login screen when you open their app and you can’t proceed unless you authenticate and have been granted access. I prefer the former, rather than the latter approach. Whichever approach you use is up to you and you can even ‘opti-test’ both to see what your customers prefer.
What is opti-testing? Well, we can dive more into that in a future article.